Network security threats seem to be unending. Broadly distributed ransomware infections, such as WannaCry, cause global damage—with billions of dollars in business losses—and in some severe cases, the shuttering of companies. These worst case scenarios are caused by cyber criminals that disable, and even delete, critical data and the supporting IT Systems. The blame for ransomware is often directed at the bad actors working to damage our companies or extort money from us by demanding a ransom. While the bad actors are the trigger, the fault for such attacks can be slightly more complex.
So what is really to blame for the massive outbreak of ransomware? That depends. But it is most often a lax software hygiene and improper vulnerability patch management that creates the very significant, and preventable, threat to businesses’ cybersecurity. Evidence shows that a large majority of attacks we’ve seen have been the result of exploiting known vulnerabilities that were identified, and had patches written to mitigate the vulnerability. Thousands of companies have fallen victim to this; while at the same time, the attacks were avoided by those businesses that took action to close the known software vulnerabilities through updates and software patching.
Of course, those that take security seriously are more effective at patching core Operating System (OS) software than those who are not. However, even the more dedicated systems managers are much less disciplined about keeping third-party software up-to-date. Third-party software works with operating systems and is written by professionals other than the operating system maker. Software like Adobe Suite, Java, iTunes and Firefox, all need consistent patching hygiene. Large and mid-sized enterprises might have tens of thousands of instances, along with hundreds of software variants, within their organizations. Small companies will even have a diverse set of software being used in daily business operations. Every piece of software, if left unpatched, increases the likelihood of a successful attack.
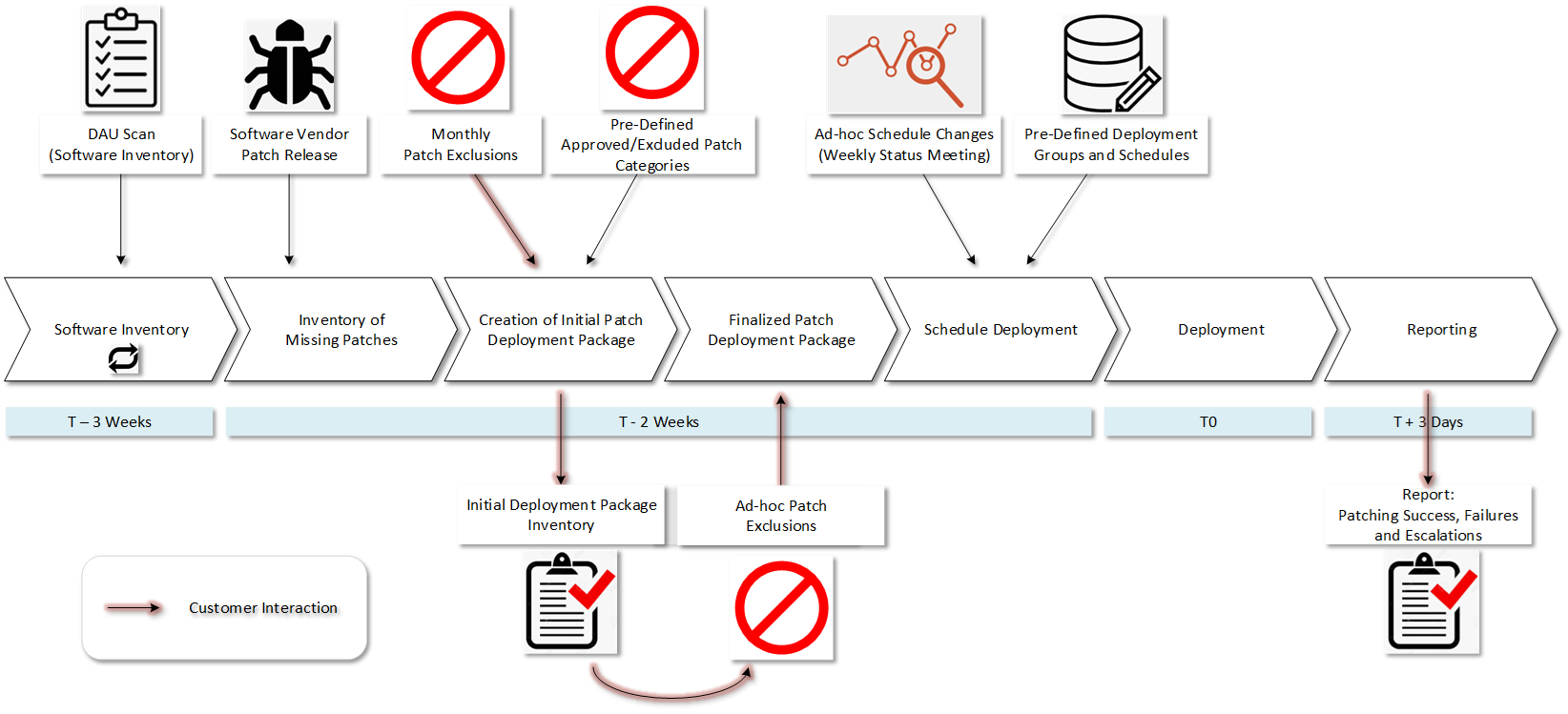
Securing software from vulnerabilities by patching is often complex and very time consuming. Many times it involves working after-hours and having system downtime. Patching takes careful planning, managed implementation, and post-deployment testing and verification. While OS patching is a critical obligation, we must not forget that it is critical to include third-party patching as part of the entire software patching process.
In our opinion, software patching is the most impactful action you can take to defend yourself and your company; however, it is not something you can do partially. If patching is to be an effective defense tool, getting it to 100% completion, or as close as possible, is key. One unpatched system is all it takes to be the source of a cascading attack.
Don’t be the next victim of bad patching practices!
Contact us today to learn more about Patchworx, our complete patch management service!