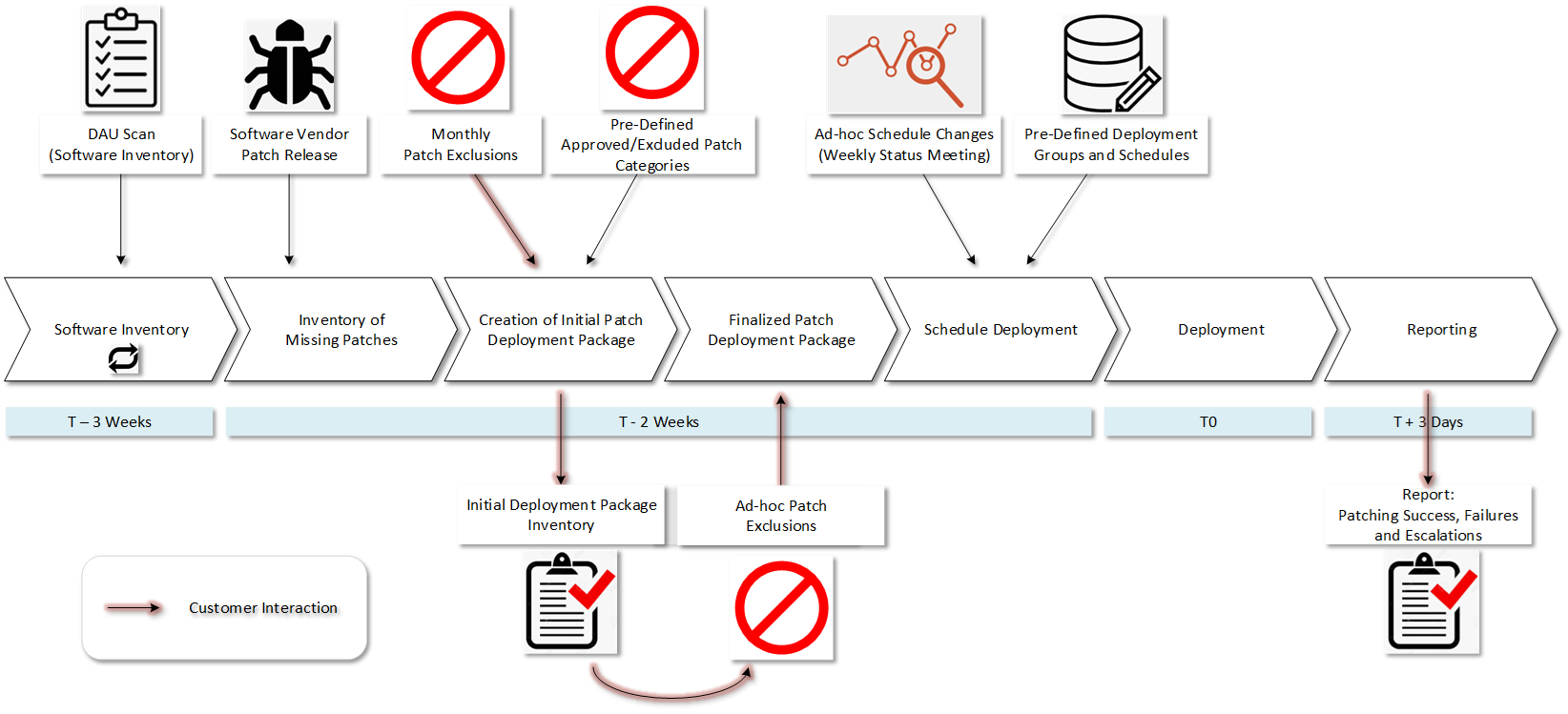
The vulnerability, found by Israeli Security Firm Check Point, resides in Microsoft’s domain name system protocol (DNS). The bug handles data used for key exchange in DNSSEC – the secure version of Windows DNS. Fortunately, Microsoft has already released a fix for the bug – which has been termed SigRed. Check Point has stated that SigRed was rated “critical, a 10 out of 10 on the common vulnerability scoring system, an industry-standard severity rating.” It has received the maximum rating due to its ‘wormable’ capabilities, allowing cybercriminals to potentially leverage it and “spread [it] from one machine to another with no human interaction.” SigRed can be transformed into the next WannaCry – A cryptoworm attack that created worldwide havoc in 2017. Microsoft has advised that every company take immediate action in patching the vulnerability. Adding on to the severity of the situation, SigRed has existed in Window’s DNS since 2003, virtually placing the majority of small and medium-sized enterprises around the globe at risk.
A statement from Chris Cartwright, Alvaka’s Senior Systems Architect
“Companies need to stay vigilant on their patching and also be aware to such issues [SigRed] by subscribing and reading security blogs daily.” – Chris Cartwright
We at Patchworx advise our clients, and others reading this blog, to immediately use Microsoft’s patch for Windows DNS if you haven’t done so already. If your IT department struggles to properly execute security patching do not hesitate to contact our qualified staff. We can guarantee your patches have been applied correctly and on time through our Patchworx solution
Original article from Wired.Com – Hack Brief: Microsoft Warns of 17-Year-Old ‘Wormable’ Bug
More information from ZDNet – DHS CISA tells government agencies to patch Windows Server DNS bug within 24h